- Increasing cyber-attack surface
- Lack of cybersecurity mindset
- Mass availability of hacking technologies within the IT ecosystem
- Unprotected legacy systems
- Increasing risks from remote access requirements by vendors and staff
When it comes to building a solid security architecture, there is no ‘one pill solves it all’ solution – no single technology can fully protect all critical assets.
Merging of the IT and OT worlds means that you need a cybersecurity platform that can:
- Address all internal and external security threats
- Provide automation to free up your specialists and allow them to work on the bigger challenges
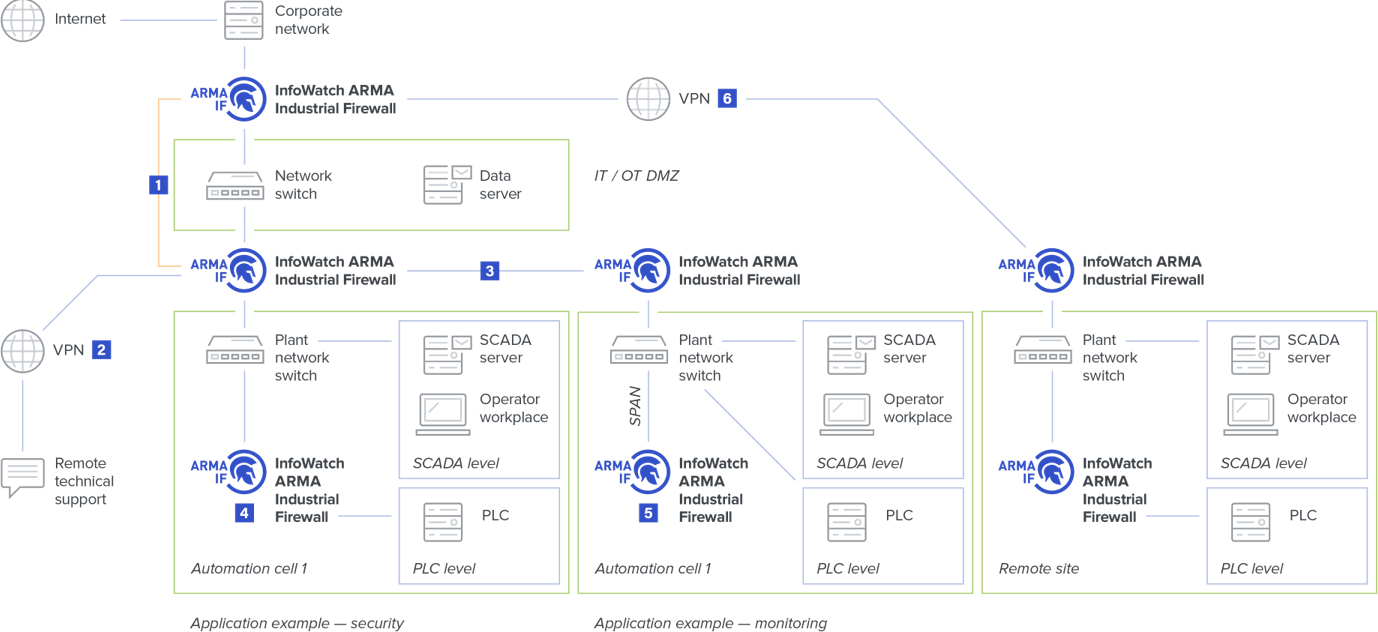
- Set up a network segmentation for your ICS to be separated from the corporate network with minimal access points between them
It is paramount to minimize control system exposure by deploying solutions that secure and optimize the industrial environment. That’s how we enable it by embedding cybersecurity within the OT environment.
Having a segmented protection throughout the network helps to reduce its vulnerability and successfully manage and mitigate risks.
InfoWatch ARMA system allows you to implement a Defense in Depth security approach: protecting networks and endpoints in OT/IT production ecosystem, responding quickly to threats and complying with regulations.
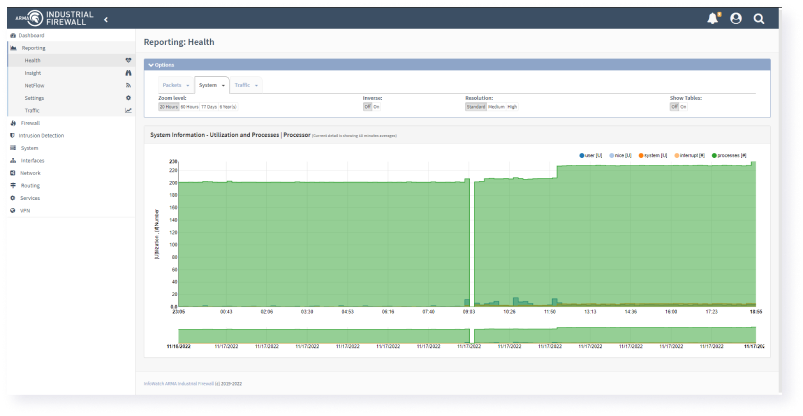
Brings in the Defense in Depth strategy based on NGFW, IDS/IPS and DPI. Helps to detect and block attacks on industrial networks, protect against unauthorized access and ensure compliance with legal requirements.
DPI for ICS Security
- Modbus TCP
- Modbus TCP x90 func. code (UMAS)
- S7 Communication plus
- OPC DA
- OPC UA
- IEC 60870-5-104
- IEC 61850-8-1 MMS
- IEC 61850-8-1 GOOSE
IT-protocols
- IPv4
- IPv6
- TCP
- UDP
- SCTP
- ICMPv4
- ICMPv6
- Ethernet
- PPP
- DHCP
- SSH
- SLL
- VLAN
- HTTP
- HTTP / 2
- SSL
- TLS
- and more
Fault-tolerance (option)
- Active / Passive cluster
- Bypass mode
- Rugged industrial hardware
Secure Remote Connection with VPN
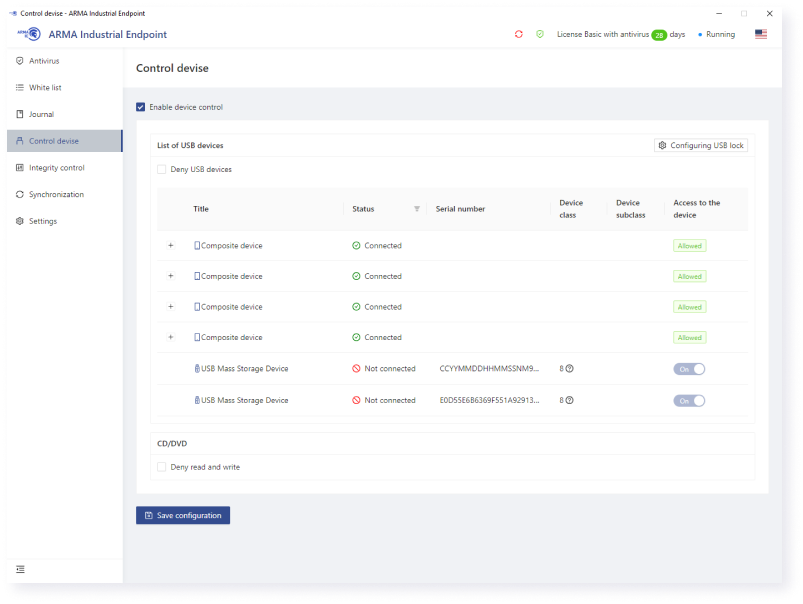
Ensuring file integrity control, removable media scanning, application whitelisting along with the antivirus security.
Continuity of ICS operation
Minimum workloads of equipment
Automation of information security processes
Empowers your team with a centralized approach to detecting and blocking threats, configuring automatic response to incidents and managing product updates of the integrated InfoWatch ARMA system.
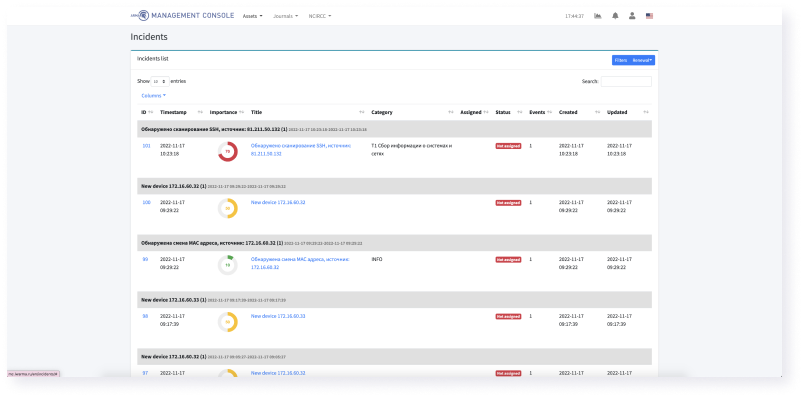
Information security incident management and investigation
- Collects information security events from industrial network and protection tools
- Shows incidents as an interconnected map of events
- Allows you to determine the beginning of a cyber attack
A whole picture of the information security state in production
- Well-aware of key differences between IT and OT requirements
- Enables secure communication between IT and OT systems and helps you meet different standards in securing your ICS
- Offers a tested and validated solution put through rigorous analysis and exposure to threats
- Deep understanding of the ICS environment and what is required to secure it
InfoWatch ARMA?
Let's talk: